Getty Images
Threat actors carried out zero-day assaults that focused Windows customers with malware for more than a year before Microsoft fixed the vulnerability that made them doable, researchers mentioned Tuesday.
The vulnerability, current in each Windows 10 and 11, causes gadgets to open Internet Explorer, a legacy browser that Microsoft decommissioned in 2022 after its getting older code base made it more and more inclined to exploits. Following the transfer, Windows made it troublesome, if not inconceivable, for regular actions to open the browser, which was first launched within the mid-Nineteen Nineties.
Tricks outdated and new
Malicious code that exploits the vulnerability dates again to no less than January 2023 and was circulating as not too long ago as May this year, in response to the researchers who found the vulnerability and reported it to Microsoft. The firm fixed the vulnerability, tracked as CVE-2024-CVE-38112, on Tuesday as a part of its month-to-month patch launch program. The vulnerability, which resided within the MSHTML engine of Windows, carried a severity score of seven.0 out of 10.
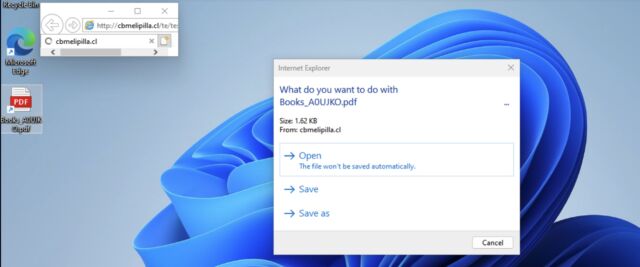
The researchers from safety agency Check Point mentioned the assault code executed “novel (or previously unknown) tricks to lure Windows users for remote code execution.” A hyperlink that appeared to open a PDF file appended a .url extension to the top of the file, for occasion, Books_A0UJKO.pdf.url, present in one of many malicious code samples.
When seen in Windows, the file confirmed an icon indicating the file was a PDF slightly than a .url file. Such information are designed to open an software laid out in a hyperlink.

Check Point
A hyperlink within the file made a name to msedge.exe, a file that runs Edge. The hyperlink, nonetheless, included two attributes—mhtml: and !x-usc:—an “old trick” menace actors have been utilizing for years to trigger Windows to open purposes similar to MS Word. It additionally included a hyperlink to a malicious web site. When clicked, the .url file disguised as a PDF opened the location, not in Edge, however in Internet Explorer.
“From there (the website being opened with IE), the attacker could do many bad things because IE is insecure and outdated,” Haifei Li, the Check Point researcher who found the vulnerability, wrote. “For example, if the attacker has an IE zero-day exploit—which is much easier to find compared to Chrome/Edge—the attacker could attack the victim to gain remote code execution immediately. However, in the samples we analyzed, the threat actors didn’t use any IE remote code execution exploit. Instead, they used another trick in IE—which is probably not publicly known previously—to the best of our knowledge—to trick the victim into gaining remote code execution.”
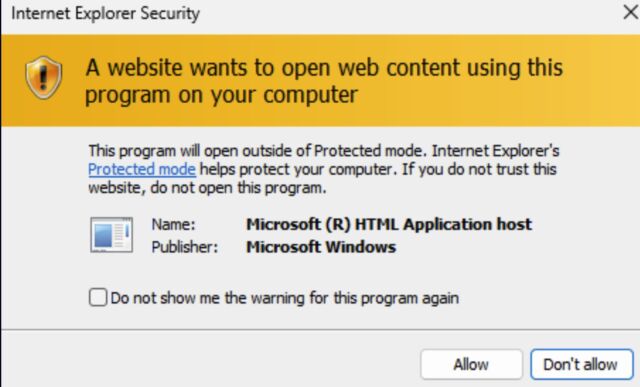
IE would then current the consumer with a dialog field asking them in the event that they wished to open the file masquerading as a PDF. If the consumer clicked “open,” Windows introduced a second dialog field displaying a obscure discover that continuing would open content material on the Windows machine. If customers clicked “allow,” IE would load a file ending in .hta, an extension that causes Windows to open the file in Internet Explorer and run embedded code.
Check Point
Check Point
“To summarize the attacks from the exploitation perspective: the first technique used in these campaigns is the “mhtml” trick, which permits the attacker to name IE as a substitute of the more safe Chrome/Edge,” Li wrote. “The second technique is an IE trick to make the victim believe they are opening a PDF file, while in fact, they are downloading and executing a dangerous .hta application. The overall goal of these attacks is to make the victims believe they are opening a PDF file, and it is made possible by using these two tricks.”
The Check Point publish consists of cryptographic hashes for six malicious .url information used within the marketing campaign. Windows customers can use the hashes to test if they’ve been focused.





